Building a strong cybersecurity program takes more than just good tools—it requires a clear, structured approach that aligns with your organization’s goals. That’s where NIST risk assessment frameworks shine. Whether you’re launching a new cybersecurity initiative or refining an existing one, NIST provides the guidance needed to confidently identify, assess, and manage the risks most relevant to your environment.
With decades of expertise behind them, NIST frameworks bring clarity to complex challenges like AI governance, ransomware defense, cloud security, and supply chain risk. They promote a consistent, repeatable process that helps teams prioritize wisely, communicate effectively with leadership, and continuously improve their security posture.
With several frameworks to choose from, understanding how they fit together—and how they apply to your specific needs—can unlock new opportunities to strengthen your cybersecurity strategy with intention and confidence. To help break it down, we’re spotlighting four essential NIST frameworks that provide a roadmap for smarter cybersecurity:
- NIST AI Risk Management Framework (AI RMF 1.0)
- NIST Ransomware Risk Management Framework (NIST IR 8374)
- NIST Security and Privacy Controls Framework (SP 800-53):
- NIST Cybersecurity Framework (CSF) 2.0:
Each of these frameworks plays a distinct role, but they all contribute to strengthening organizational resilience. The table below provides a high-level overview of each framework, its primary focus, who should use it, key risk areas it addresses, and how it aligns with other NIST frameworks:
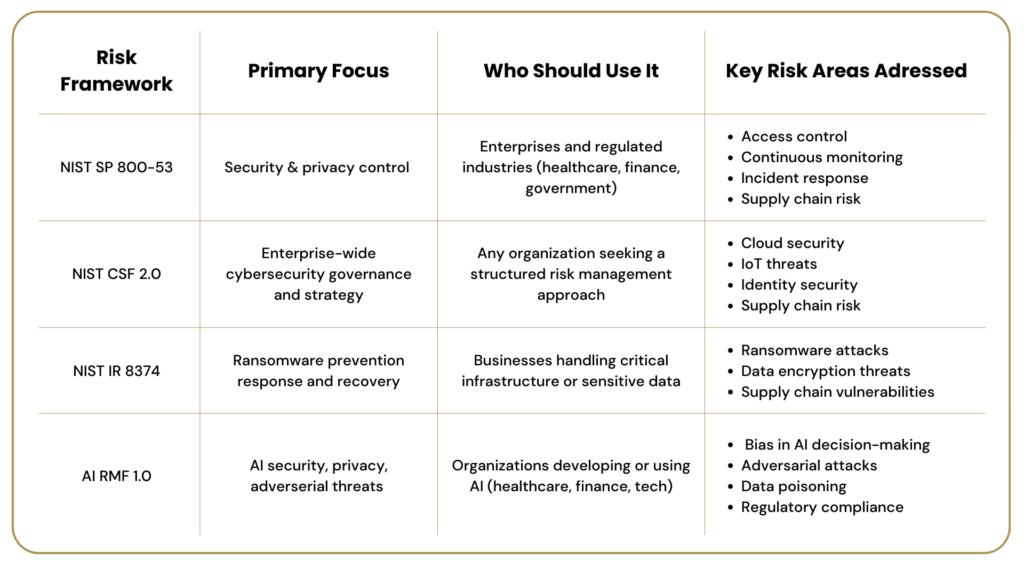
While their focus varies, they provide essential guidance for managing risks, enhancing security measures, and safeguarding critical systems. By aligning your strategy with these best practices, you’re not just checking a compliance box—you’re reinforcing your defenses, protecting vital assets, and building a foundation for long-term resilience.
NIST Security and Privacy Controls Framework
NIST SP 800-53 helps organizations define clear security controls that map directly to regulatory requirements, industry standards, and evolving cyber risks. It also prioritizes supply chain security, recognizing that many breaches now stem from third-party vulnerabilities. Beyond cybersecurity, SP 800-53 integrates privacy protections, ensuring that security measures don’t just lock down systems but also safeguard sensitive data. This makes it especially valuable for organizations navigating compliance-heavy industries like healthcare, finance, and technology. For companies trying to balance security, compliance, and efficiency, SP 800-53 serves as the perfect roadmap. As a result, organizations that strategically map these controls to their business objectives can streamline security operations, avoid redundancies, and stay ahead of emerging threats without unnecessary complexity.
How NIST 800-53 Stands Apart from Other Cybersecurity Frameworks
Unlike CSF 2.0, which provides high-level, outcome-focused guidance, SP 800-53 is highly detailed and prescriptive, offering a comprehensive catalog of security controls that organizations can implement. Originally developed for federal agencies and contractors, it has expanded to support private-sector industries in meeting compliance and security requirements. Covering a wide range of security topics—including access controls, supply chain risk, continuous monitoring, and incident response—SP 800-53 stands out as the most granular and detailed of all NIST frameworks.
How It Complements Other Frameworks:
- Acts as the control backbone for CSF 2.0 and provides the technical safeguards needed to meet security goals.
- Maps directly to regulatory requirements, such as HIPAA, PCI-DSS, and FedRAMP, helping organizations streamline compliance.
NIST Cybersecurity Framework 2.0
CSF 2.0 pushes organizations to make risk management a core part of decision-making, ensuring clear accountability, defined risk appetites, and cybersecurity policies that align with business objectives. CSF 2.0 strengthens guidance on assessing third-party risks, implementing vendor security requirements, and ensuring ongoing monitoring of supplier security practices. With high-profile supply chain attacks becoming more frequent, businesses that fail to lock down their vendor relationships are leaving a massive gap in their defenses.
The framework also sharpens its focus on cloud security, AI risks, IoT vulnerabilities, and identity-based threats—all critical areas that attackers are actively exploiting. Furthermore, organizations that adopt CSF 2.0 are helping to future-proof their cybersecurity posture, ensuring they can detect, respond to, and recover from threats before they spiral into full-blown crises.
Cybersecurity isn’t static, and neither is CSF 2.0. It gives organizations a clear structure to stay ahead of emerging threats, making security a business priority, not just an IT function. Those that embrace these principles will be better positioned to manage cyber risk—not just react to it.
How NIST CSF 2.0 Stands Apart from Other Cybersecurity Frameworks
CSF 2.0 is broader and more flexible than SP 800-53, providing a strategic cybersecurity roadmap that organizations can tailor to their specific needs rather than prescribing individual security controls. A key differentiator is the addition of the Govern function, which emphasizes leadership oversight and enterprise-wide cybersecurity governance, ensuring that security is integrated into business decision-making. Unlike the AI RMF, which focuses exclusively on AI-related risks, CSF 2.0 applies to all cybersecurity threats across an organization, including cloud security, IoT vulnerabilities, ransomware, and supply chain risks.
One of the key outcomes of CSF 2.0 is its maturity model, which categorizes organizations into one of four maturity levels, providing a clear benchmark for leadership and boards. This structured assessment allows organizations to set improvement targets, track progress, and align their cybersecurity strategy with long-term business objectives—while also signaling to customers, partners, and stakeholders how seriously they prioritize cybersecurity. The ability to transparently demonstrate progress and intent helps build trust and reinforces an organization’s commitment to protecting sensitive data and system.
How It Complements Other Frameworks:
- Serves as an umbrella framework under which organizations can incorporate SP 800-53 controls, AI RMF, and the Ransomware Framework to address specific risks.
- Helps businesses prioritize cybersecurity investments and maturity improvements while ensuring alignment with regulatory and risk management requirements.
NIST AI Risk Management Framework
AI is revolutionizing everything from finance and healthcare to cybersecurity itself, but it’s also introducing new risks that most organizations aren’t fully prepared for. Unlike traditional cybersecurity threats, AI-related risks don’t just come from hackers—they can stem from biased algorithms, privacy violations, and even unintended system failures. A poorly governed AI system can leak sensitive data, make unfair decisions, or even disrupt entire industries.
That’s why NIST’s AI RMF is so crucial. It helps organizations identify, assess, and manage AI risks, ensuring AI is developed and deployed responsibly and securely. As a result, the AI RMF has broken down AI risks into three broad categories:
- Harm to Organizations – AI failures can lead to data breaches, financial losses, and operational disruptions. Poorly secured AI models could be manipulated for fraud or used to leak sensitive data, creating serious security and compliance risks.
- Harm to People – AI decisions can introduce bias, privacy violations, or safety concerns. In industries like healthcare and finance, a flawed AI model can deny someone critical care, misdiagnose an illness, or unfairly reject a loan application—leading to real-world harm and legal exposure for businesses.
- Harm to Ecosystems – AI failures don’t just affect individual companies—they can cascade into supply chain disruptions, regulatory noncompliance, or reputational damage. Without strong governance, AI risks can ripple across industries, eroding trust and stability.
A Structured Approach to AI Risk
To help organizations take control of these risks, the AI RMF provides a clear, actionable framework that integrates seamlessly into existing cybersecurity programs. The framework is built around four core functions—Govern, Map, Measure, and Manage—designed to ensure AI remains secure, compliant, and ethically responsible.
The Govern function ensures AI risk oversight is embedded into policies, ethical guidelines, and leadership decision-making rather than being treated as an afterthought. Strong governance structures help organizations define accountability and align AI risk management with broader enterprise risk strategies, much like the “Govern” function in NIST CSF 2.0.
The Map function provides organizations with a structured way to identify and analyze their AI deployments. It emphasizes defining an AI system’s scope, purpose, and risk scenarios at every stage of its lifecycle. Without a clear mapping process, organizations risk deploying AI in ways that introduce security gaps, compliance violations, or ethical concerns.
The Measure function establishes continuous monitoring and assessment, ensuring organizations can detect vulnerabilities, assess model fairness, and track AI risks over time. Unlike traditional cybersecurity monitoring, AI requires specialized risk metrics, such as measuring adversarial robustness, model drift, and unintended bias. Organizations that fail to implement ongoing AI assessments risk allowing AI systems to degrade in accuracy, security, and ethical reliability.
The Manage function ensures that AI risks are proactively mitigated and addressed as AI models evolve. Organizations must take an adaptive approach, continuously refining AI security strategies, updating controls, and integrating AI risk management into broader cybersecurity and compliance programs. When AI risk is not actively managed, organizations open themselves up to financial loss, regulatory penalties, and reputational harm.
How AI RMF Stands Apart from Other Cybersecurity Frameworks
Unlike traditional cybersecurity frameworks that focus on securing IT systems and networks, AI RMF is tailored to address the unique risks of artificial intelligence, including bias in decision-making, adversarial attacks, privacy concerns, and regulatory compliance in AI-driven applications. It bridges the gap between AI security and broader enterprise risk management while emphasizing ethical considerations—an area not covered in other NIST security frameworks.
How It Complements Other Frameworks:
- Works alongside CSF 2.0 and SP 800-53 by adding a layer of AI-specific risk considerations to existing cybersecurity programs.
- Helps organizations adapt traditional security controls to the challenges introduced by AI.
NIST Ransomware Risk Management Framework
Ransomware isn’t just an IT issue—it’s an operational crisis waiting to happen. Entire businesses have been brought to a standstill, customer data has been locked away behind ransom demands, and organizations have lost millions trying to recover. The threat isn’t slowing down, and with ransomware groups evolving their tactics, companies need a structured, proactive defense strategy.
NIST IR 8374 lays out a clear roadmap for organizations to assess, prepare for, and defend against ransomware attacks. The framework is built around the five core functions of the NIST CSF:
- Identify focuses on understanding the risks ransomware poses to systems, data, and critical operations. Without a clear picture of vulnerabilities, organizations can’t build effective defenses.
- Protect emphasizes access controls, employee security training, and encryption to keep ransomware from gaining a foothold. Many attacks start with compromised credentials or unpatched systems, making strong protection measures a non-negotiable.
- Detect ensures organizations continuously monitor for ransomware indicators—such as unusual file encryption activity or unauthorized access attempts. Early detection can mean the difference between isolating an attack and losing everything.
- Respond guides businesses in containing and neutralizing ransomware attacks through predefined response plans. Without a tested, well-practiced response strategy, companies can waste precious time scrambling to react—often making the situation worse.
- Recover is about getting systems back online as quickly and securely as possible. Reliable, tested backups are a must, but so is having a plan to restore operations without reinfecting systems.
Beyond these core functions, NIST IR 8374 reinforces the importance of supply chain security. Many ransomware attacks don’t just target organizations directly—they infiltrate through third-party software providers, vendors, or cloud services. That’s why it’s critical to assess supplier risk, enforce strong security requirements in vendor contracts, and continuously monitor supplier security practices.
Defending against ransomware isn’t just about stopping an attack before it starts—it’s also about limiting damage when one inevitably slips through. Offline and immutable backups ensure that even if data is encrypted, a clean version is available for recovery. Multi-factor authentication (MFA) reduces the risk of attackers gaining access to critical systems through stolen credentials. And implementing a zero-trust architecture—where no one inside or outside the network is automatically trusted—makes it much harder for ransomware to spread unchecked.
How NIST IR 8374 Stands Apart from Other Cybersecurity Frameworks
While CSF 2.0 and SP 800-53 provide broad cybersecurity guidance, NIST IR 8374 is specifically designed to tackle ransomware threats, focusing on prevention, response, and recovery. It tailors security controls to counter encryption-based extortion attacks, helping organizations fortify their defenses against this growing risk. By prioritizing backup integrity, incident response planning, and real-time threat detection, the framework ensures businesses can recover quickly and minimize operational disruption in the event of an attack.
How It Complements Other Frameworks:
- Provides a targeted security strategy for ransomware that fits within the broader CSF 2.0 framework.
- Aligns with SP 800-53 controls but distills them down to ransomware-specific applications
Unifying NIST Frameworks for Effective Risk Management
NIST frameworks work together to create a comprehensive, layered approach to cybersecurity risk management. Each framework serves a distinct role, ensuring organizations can address risks related to AI, ransomware, security controls, and enterprise-wide cyber resilience. AI RMF 1.0, IR 8374, SP 800-53, and CSF 2.0 are standalone frameworks, each addressing specific aspects of risk management. However, they can also be complementary, enabling businesses to integrate their security strategies across different domains for a more comprehensive approach.
Drummond helps organizations bridge these frameworks, ensuring seamless implementation tailored to specific security and compliance needs. Our expertise in risk assessment, security controls, and regulatory alignment allows businesses to adopt NIST best practices with confidence. Contact our team today to strengthen your security posture with a strategic, risk-based approach.
