With healthcare organizations increasingly shifting to cloud-based platforms, safeguarding sensitive patient data is more critical than ever. While cloud environments offer scalability and flexibility, they also present unique security challenges. In 2024 alone, 82% of data breaches involved data stored in cloud environments.
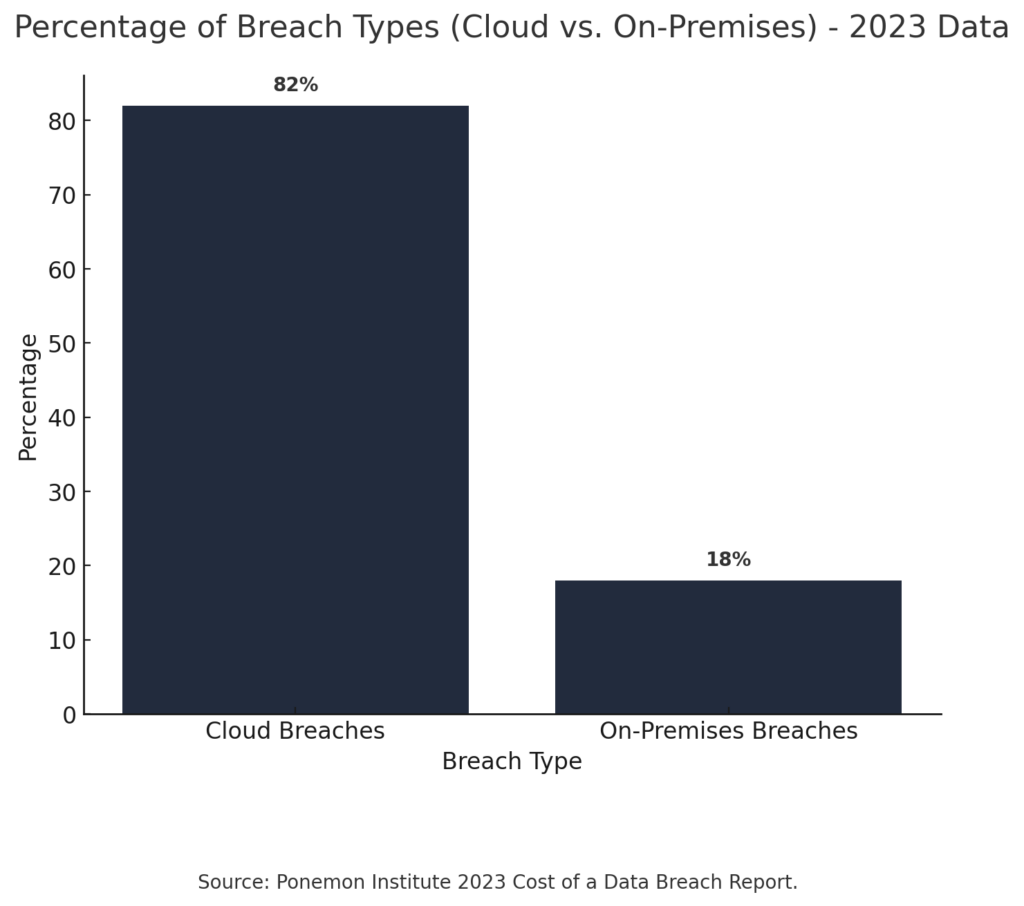
This is because while regulations like HIPAA and HITECH set essential security standards, relying solely on their compliance can still leave significant gaps in your data protection. As a result, adopting best practices in cloud penetration testing allows healthcare organizations to elevate their security stance from merely reactive to proactive, helping them identify and address vulnerabilities before they can be exploited. Moreover, effective security is not static—it demands constant improvement and adaptation to new risks. This approach not only helps maintain compliance but also fortifies cloud systems against the types of attacks most often aimed at healthcare, such as ransomware, data theft, and credential compromise.
To help you achieve a more robust security posture, we’ll explore the role of cloud penetration testing in healthcare and cover essential practices that go beyond compliance to bolster overall security.
Regular Testing to Identify Vulnerabilities Early
Establishing a regular testing cadence is essential for effective cloud penetration testing. In dynamic cloud environments, where configurations, applications, and user access can change frequently, regular penetration testing identifies vulnerabilities that might arise from these changes. As a result, healthcare organizations should consider testing on a quarterly basis or whenever significant system updates occur, especially when cloud infrastructure hosts critical patient data. Additionally, testing after major updates, new integrations, or changes in cloud configurations helps ensure that no new vulnerabilities are introduced. A consistent testing schedule allows healthcare organizations to stay ahead of evolving threats, preventing potential security gaps from widening over time.
Adapting Testing to Address Healthcare-Specific Threats
Healthcare data is one of the most sought-after targets for cybercriminals due to its valuable personal and medical information. In fact, the number of reported data breaches in 2024 (386 as of end of September) is on pace with 2023’s record high figures (the highest number of healthcare data breaches on record). To fortify security measures against an increasing number of threats, healthcare organizations must tailor cloud penetration testing to address the attacks most relevant to their sector. This approach means understanding the types of attacks commonly directed at healthcare systems and focusing testing efforts on these specific threats.
A tailored approach to penetration testing could include simulating attacks like ransomware, where attackers seek to lock patient data and demand payment to release it. Another scenario might involve testing data exfiltration techniques, where cybercriminals attempt to access and extract patient information without detection. Testing these scenarios helps organizations understand how their systems will respond to real-world threats and where additional protective measures may be needed.
By customizing penetration testing to focus on healthcare-specific threats, organizations gain a clearer view of vulnerabilities that might go undetected with general testing. This industry-specific approach helps close potential security gaps and demonstrates a commitment to safeguarding patient data in a sector where data privacy is paramount.
Ensuring Comprehensive Coverage of Cloud-Specific Vulnerabilities
Cloud environments introduce unique challenges that require a thorough and targeted testing approach. Common issues like misconfigurations, weak access controls, and data exposure risks are prevalent in cloud platforms. Addressing these vulnerabilities through penetration testing creates a more secure foundation for storing healthcare data.
To mitigate these risks, healthcare organizations should focus on configuration checks and robust access control measures. Misconfigurations—such as open storage buckets or poorly defined access permissions—are frequent sources of data breaches in cloud systems. Testing should confirm that configurations align with security best practices and that only authorized users can access sensitive patient data. Since cloud environments require distinct security protocols compared to traditional on-premises systems, integrating cloud-native security tools during testing can yield more accurate insights. For instance, cloud-native identity and access management (IAM) tools enable testers to verify that access permissions are correctly set and enforced.
Additionally, testing for data leakage through unsecured APIs or inadequately protected data stores is essential. This step allows organizations to identify areas where patient information may be unintentionally exposed, enabling them to apply stronger controls. These comprehensive tests tailored to cloud-specific vulnerabilities reinforces security for healthcare organizations, reducing the likelihood of breaches caused by overlooked misconfigurations or weak permissions.
Enhancing Cloud Security Through Penetration Testing Insights
Integrating test insights into daily security operations transforms an organization’s approach to security, creating a proactive environment that can swiftly adapt to emerging threats. By sharing these insights across departments—such as IT, compliance, and clinical teams—healthcare organizations establish a collaborative, layered defense. Test results not only highlight specific vulnerabilities but also reveal patterns and recurring risks, enabling each department to contribute to a coordinated, organization-wide security posture.
With test insights guiding daily operations, the organization is better positioned to anticipate potential threats and preemptively strengthen its defenses. Yet, the real value of penetration testing goes beyond merely identifying these vulnerabilities; it lies in prioritizing remediation efforts based on each issue’s severity and impact. Actionable insights from testing reports empower IT teams to address high-risk issues, such as misconfigured databases holding sensitive information, while planning for ongoing management of lower-priority vulnerabilities.
Verification testing, or re-testing, then confirms that all critical vulnerabilities have been resolved, completing a cycle of continuous improvement. This iterative process of incorporating, acting on, and verifying test insights builds a stronger foundation for defense against current and future security challenges, laying the groundwork for a proactive and resilient security strategy.
The Long-Term Benefits of Proactive Cloud Security in Healthcare
Adopting best practices for cloud penetration testing provides healthcare organizations with far-reaching benefits beyond basic compliance. Regular testing and proactive risk management significantly reduce the likelihood of data breaches by addressing vulnerabilities before they can be exploited. This approach builds a foundation of trust with patients, who are increasingly aware of data privacy issues and expect healthcare providers to protect their information.
Proactive cloud penetration testing also positions healthcare organizations to better handle audits and regulatory requirements, demonstrating a commitment to continuous improvement in data protection. As the healthcare sector continues to evolve with technological advances, maintaining a strong security posture through proactive testing not only protects sensitive data but also fosters trust and transparency with patients and partners alike.
Key Takeaways
During a time where healthcare data security is critical, healthcare organizations must prioritize proactive cloud penetration testing. Compliance with HIPAA, HITECH, and similar regulations is essential, but it should be the beginning rather than the end of a robust security strategy. By following best practices in cloud penetration testing—establishing regular testing schedules, focusing on healthcare-specific threats, covering cloud-specific vulnerabilities, integrating testing within broader security initiatives, and acting swiftly on results—healthcare organizations can protect sensitive patient data and stay ahead of emerging threats. Through a combination of regular assessments, tailored testing, and prompt remediation, healthcare providers can create a resilient cloud security framework that adapts to evolving threats, ensuring a secure and compliant environment for both their operations and the patients they serve.
